History of Computing
Homework Help & Tutoring
We offer an array of different online History of Computing tutors, all of whom are advanced in their fields and highly qualified to instruct you.
History of Computing
The Enigma Code
Introduction
The work of breaking the German Enigma code has been made more famous recently through the "Imitation Game" screenplay. Hollywood chose to focus on the life and work of Alan Turing, but how did the code actually work? This article will examine how Enigma messages were encrypted and decrypted.
Background
The Enigma machine was originally invented and developed by an engineer named Arthur Schierbus.1 Initially used by Schierbus’ corporation “Chiffriermaschinen Aktiengesellschaft”, it attracted the interest of the German military and was introduced first to the Navy during the 1920s.2 By 1933 the growing WehrMacht had implemented Enigma encryption techniques in all branches. The machine was gradually improved and refined as the escalation of armed conflicts between Germany and its European neighbours led to an increasing need of sending encrypted messages. An estimate gives a number of 100,000 machines in use at the outbreak of WWII in 1939.3
The Machine
A model of the machine can be found in Figure 1

Figure 1. An Enigma machine4
The input is given by the manual keyboard on the top. The letter goes through the plugboard, through three rotors forward and then through the same rotors in the reverse order, before the output is inidicated by a red diode lighting up on the front. This circuitry is shown in even more detail in Figure 2.
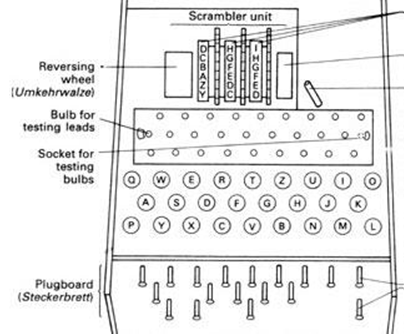
Figure 2. Enigma Machine circuitry5
The rotors are alphabetic wheels, where each letter is converted to another, as shown in Figure 3.
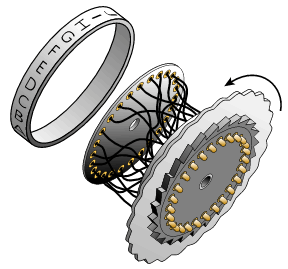
Figure 3. An Enigma rotor5
The output for a given letter input depends on how the rotor is set up, and the code for this would change every day based on codes sent out to the radio operators. Additionally, the rotor changes its setting for every letter in the message. In all, the letter is converted 7 times, twice for each reflector and by the reflector.
This gives a fairly sizeable number of output combinations, but not quite enough to satisfy the needs of the German army. They added a plugboard on the front, as indicated in Figure 4.
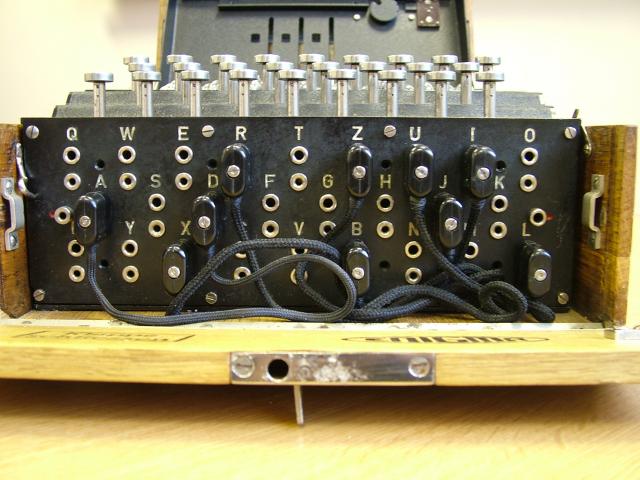
Figure 4. Enigma machine plugboard6
The plugboard makes a further conversion, where certain letters are converted to others. Up to 13 pairs can be used, and the normal mode was to set it up with 10 connectors; so in all, the Germans could alter each of:
- The ordering of the rotors
- The reflector and ring settings
- The positions in each rotor
- The ten cables on the plugboard
This yields a number of 1023 possible outputs for a letter.5 This would certainly explain why the Germans felt that their code as “unbreakable”.
Example
The encryption of a message is, as mentioned, highly dependent on the setup of the machine. The code for specifying the setup could look like this:7
215 AAA FRA "ABIRUXKP
This means:
- Use left rotor 2 (out of five)
- Use middle rotor 1
- Use right rotor 5
- Set the ring at AAA
- Set the rotors at F, R and A, respectively
- Plug A to B, I to R, U to X and K to P”
This converts
TWENTYFOURHOURANSWERSCOM
into
gvksd zshpd ackcq pgygm oftb
The simulation provided by Daniel Palloks at the Humboldt University of Berlin, Department of Physics.8
Apart from the materials cited below, on a level appropriate for a student seeking college homework help, an interesting and relevant online tutorial for computing history is offered by MIT's OpenCourseWare and is titled The History of Computing.
To fulfill our tutoring mission of online education, our college homework help and online tutoring centers are standing by 24/7, ready to assist college students who need homework help with all aspects of the history of computing. Our computer science tutors can help with all your projects, large or small, and we challenge you to find better online history of computing tutoring anywhere.
References
[1] http://en.wikipedia.org/wiki/Enigma_machine – Enigma Machine - Wikipedia.
[2] http://www.bbc.co.uk/history/topics/enigma - BBC history - BBC
[3] http://ww2db.com/battle_spec.php?battle_id=92 – World War II DataBase.
[4] Wilcox, J.: Solving the Enigma. History of the Cryptanalytic Bombe. Center for Cryptologic History, National Security Agency, 2006.
[5] http://www.cryptomuseum.com/crypto/enigma/working.htm - Crypto Museum, Netherlands.
[6] http://gallery.nen.gov.uk/asset652634-.html - National Education Network.
[7] Oberzalek, M.: Enigma – a very famous story of cryptology. http://www.mlb.co.jp/linux/science/genigma/enigma-referat/
[8] http://people.physik.hu-berlin.de/~palloks/js/enigma/ - Humboldt University, Berlin.
College History of Computing Homework Help
Since we have tutors in all History of Computing related topics, we can provide a range of different services. Our online History of Computing tutors will:
- Provide specific insight for homework assignments.
- Review broad conceptual ideas and chapters.
- Simplify complex topics into digestible pieces of information.
- Answer any History of Computing related questions.
- Tailor instruction to fit your style of learning.
With these capabilities, our college History of Computing tutors will give you the tools you need to gain a comprehensive knowledge of History of Computing you can use in future courses.
24HourAnswers Online History of Computing Tutors
Our tutors are just as dedicated to your success in class as you are, so they are available around the clock to assist you with questions, homework, exam preparation and any History of Computing related assignments you need extra help completing.
In addition to gaining access to highly qualified tutors, you'll also strengthen your confidence level in the classroom when you work with us. This newfound confidence will allow you to apply your History of Computing knowledge in future courses and keep your education progressing smoothly.
Because our college History of Computing tutors are fully remote, seeking their help is easy. Rather than spend valuable time trying to find a local History of Computing tutor you can trust, just call on our tutors whenever you need them without any conflicting schedules getting in the way.